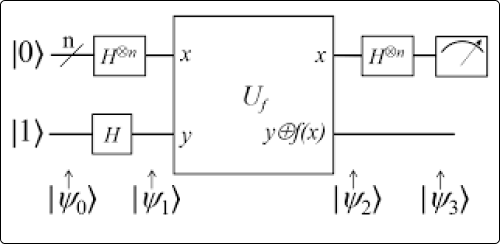
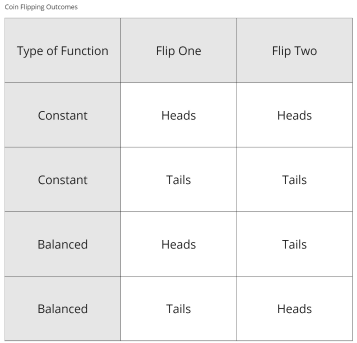
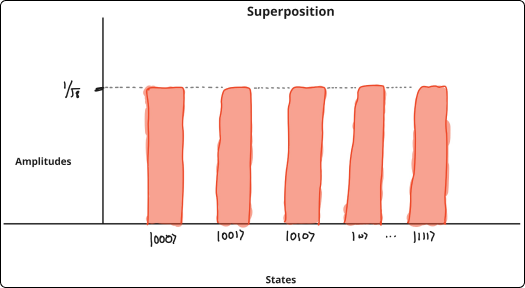
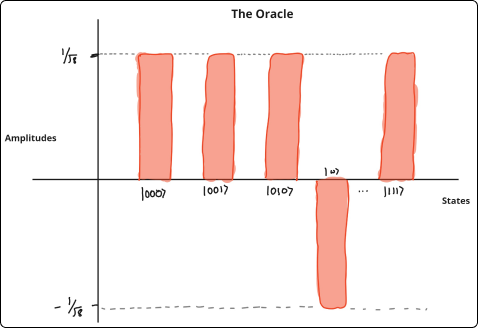
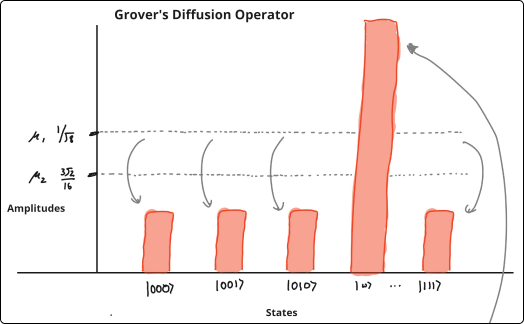
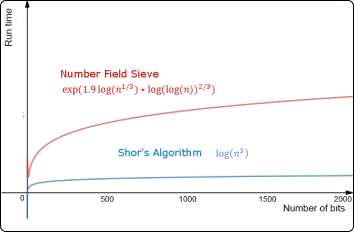
Say you have a coin, and you want to see if it's biased or not. In this hypothetical situation, the coin flip outcomes are strictly probabilistic; if biased, you would get the same outcome twice; otherwise, you would get different outcomes.
The table shows you would have four different scenarios based on two flips. You could get HH or TT, both of which indicate that the coin is biased, or you could get either HT or TH, which would suggest that the coin is fair.